IAM:
IAM stands for Identity and Access Management. It is a web service that helps you securely control access to AWS resources. With IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.
IAM enables you to grant permissions to users or groups to access resources like EC2 instances, S3 buckets, RDS databases, and many more. By using IAM, you can provide users with only the necessary permissions they require to perform their job functions, without granting them excessive privileges that can be a security risk.
In summary, IAM is a fundamental component of AWS security, and it helps you manage access to your AWS resources securely and efficiently.

Task1:
Create an IAM user with username of your own wish and grant EC2 Access. Launch your Linux instance through the IAM user that you created now and install jenkins and docker on your machine via single Shell Script.
Log in to the AWS Management Console and navigate to the IAM service.
- Click on "Users" from the left-hand menu and then click on the "Add user" button.
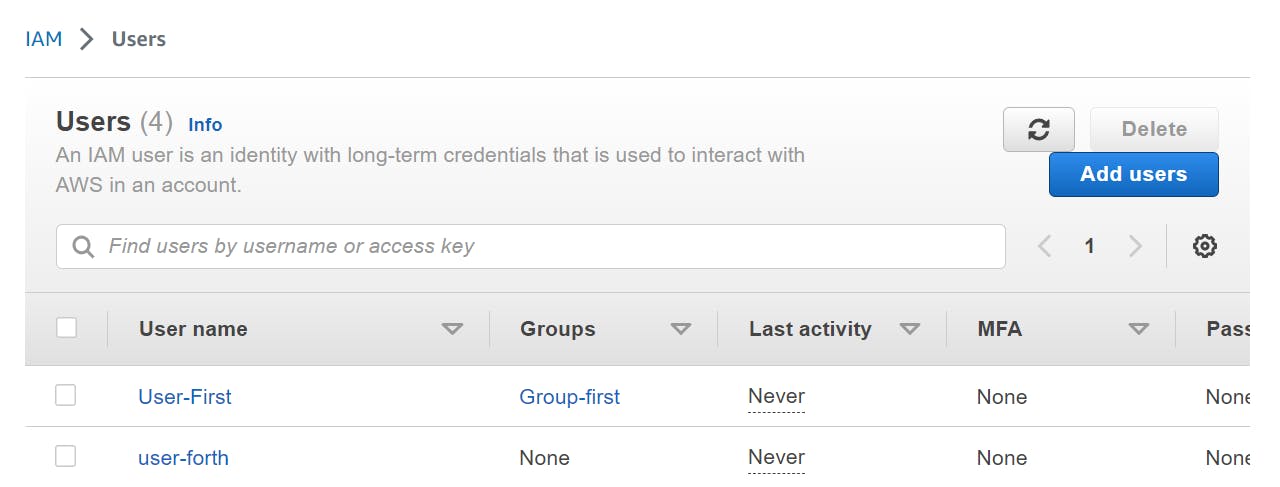
- Enter a username of your choice and select "Programmatic access" and "AWS Management Console access" as the access type.

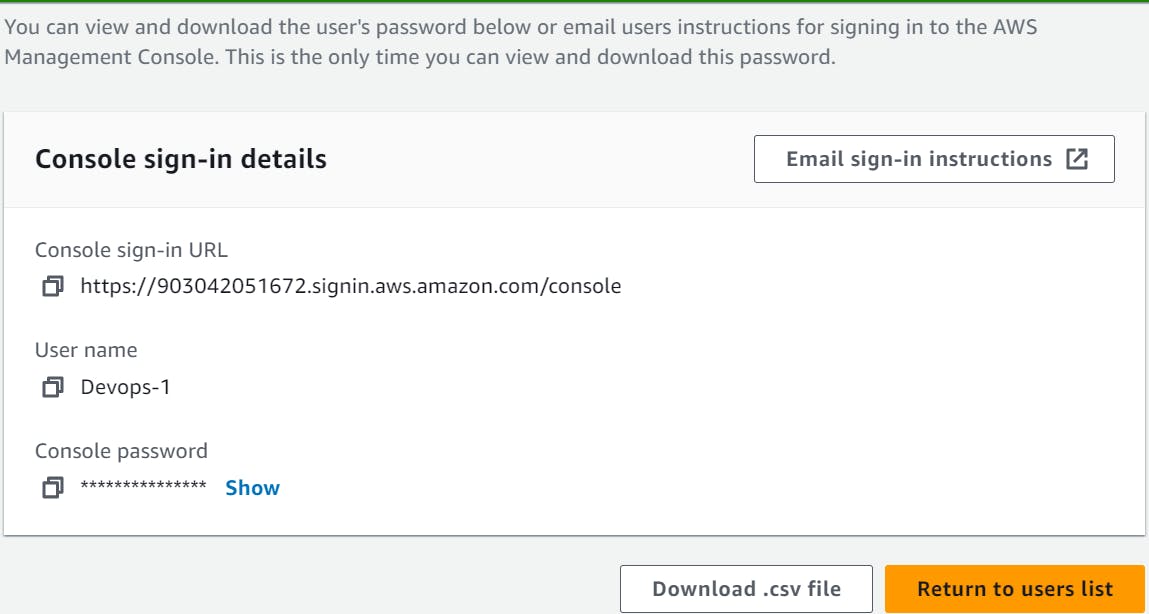
Set a custom password or let AWS generate one for you, and then click "Next: Permissions".
On the "Set permissions" page, click "Attach existing policies directly".
Search for "AmazonEC2FullAccess" and select the policy.
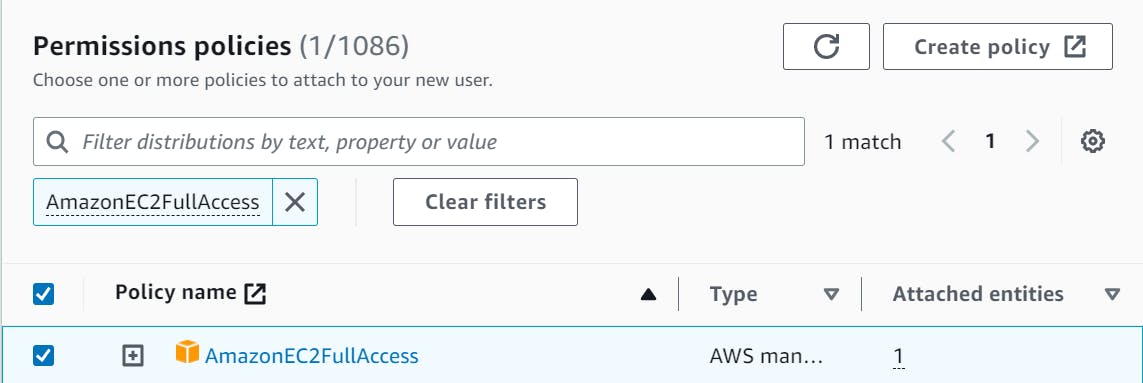
Click on "Next: Tags" and then on "Next: Review".
Review the user's details and permissions, and then click "Create user".
Note down the Access key ID and Secret access key for the user as you will need it later.
Log in to the AWS Management Console and navigate to the EC2 service.
Click on "Launch Instance" and select an Amazon Linux 2 AMI.
In the "Configure Instance Details" page, select the IAM user that you created earlier in the "IAM role" field.
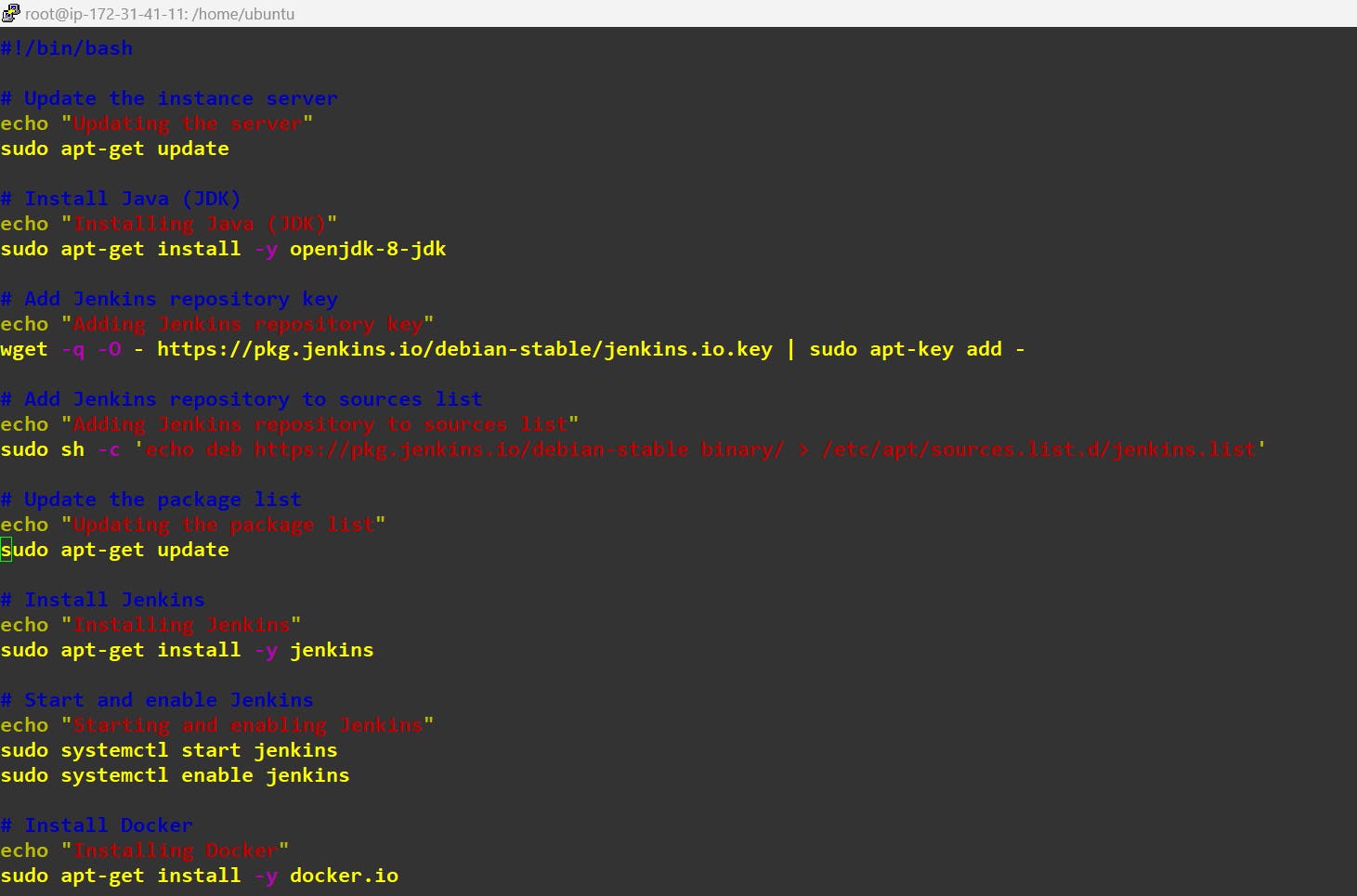
Write script:
#!/bin/bash
# Update the instance server
echo "Updating the server"
sudo apt-get update
# Install Java (JDK)
echo "Installing Java (JDK)"
sudo apt-get install -y openjdk-8-jdk
# Add Jenkins repository key
echo "Adding Jenkins repository key"
wget -q -O - https://pkg.jenkins.io/debian-stable/jenkins.io.key | sudo apt-key add -
# Add Jenkins repository to sources list
echo "Adding Jenkins repository to sources list"
sudo sh -c 'echo deb https://pkg.jenkins.io/debian-stable binary/ > /etc/apt/sources.list.d/jenkins.list'
# Update the package list
echo "Updating the package list"
sudo apt-get update
# Install Jenkins
echo "Installing Jenkins"
sudo apt-get install -y jenkins
# Start and enable Jenkins
echo "Starting and enabling Jenkins"
sudo systemctl start jenkins
sudo systemctl enable jenkins
# Install Docker
echo "Installing Docker"
sudo apt-get install -y docker.io
# Add the Jenkins user to the Docker group
echo "Adding the Jenkins user to the Docker group"
sudo usermod -aG docker jenkins
# Start and enable Docker
echo "Starting and enabling Docker"
sudo systemctl start docker
sudo systemctl enable docker
Finally give required permission:
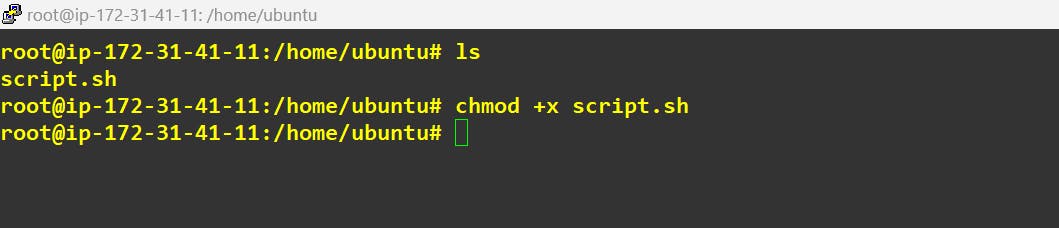
Finally Execute it:
Task2:
In this task you need to prepare a devops team of avengers. Create 3 IAM users of avengers and assign them in devops groups with IAM policy.

Here are the steps you can follow:
Log in to your AWS console and go to the IAM service.
Click on the "Groups" tab on the left sidebar and then click on the "Create New Group" button.
- Choose a name for your DevOps group, such as "Shaktiman DevOps".
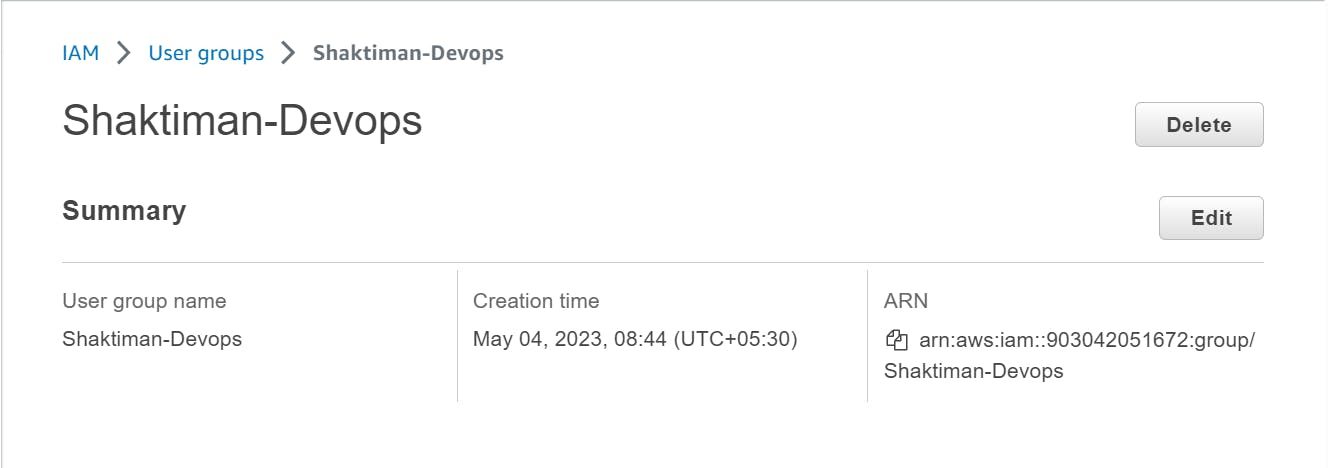
- On the "Attach Policy" page, search for and select the policies you want to assign to the group. For a DevOps group, you may want to include policies such as "AmazonEC2FullAccess", "AmazonECS_FullAccess", "AmazonS3FullAccess", and "AWSLambda_FullAccess".
- Click on "Create Group" to create the Shaktiman-Devops group.
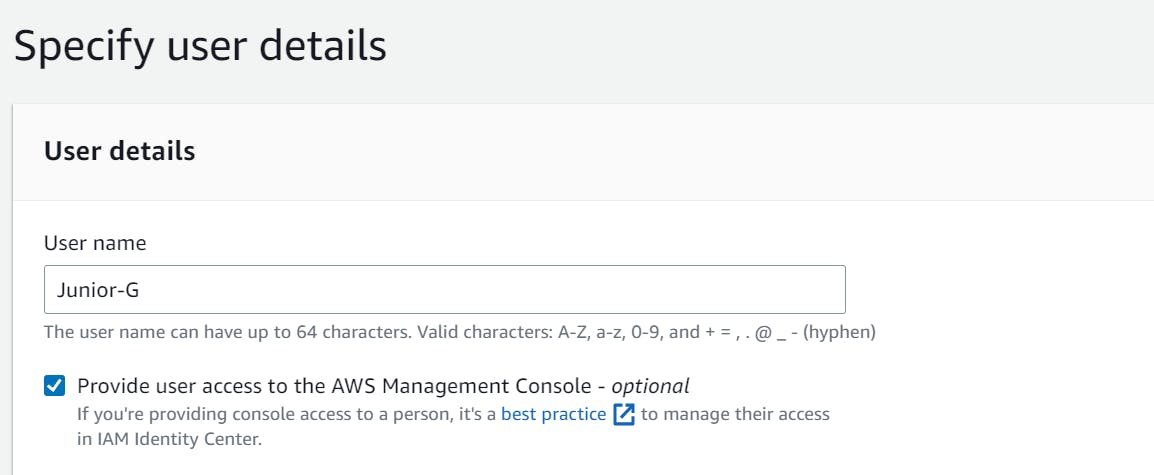
Click on the "Users" tab on the left sidebar and then click on the "Add user" button.
Choose a username for the first IAM user, such as "JuniorG".
- On the "Set Permissions" page, select "Add user to group" and choose the DevOps group you created in step 3.
- Click on "Next: Tags" and add any relevant tags.

- Repeat the same for another user too.
