ConfigMaps:
A ConfigMap in Kubernetes is an object that allows you to store configuration data that can be accessed by your application containers. It provides a way to decouple configuration data from your application code, making it easier to manage and update the configuration of your application without having to redeploy it.
A ConfigMap can store key-value pairs, where the key represents the name of a configuration parameter, and the value is the value of that parameter. You can create a ConfigMap using YAML files or through the Kubernetes API.
Overall, ConfigMaps are a powerful feature of Kubernetes that enable you to manage your application's configuration in a more flexible and scalable way. By using ConfigMaps, you can easily and consistently configure your applications, making it easier to manage and scale your Kubernetes deployments.
1.ConfigMap - Volume:
This approach involves creating a volume from a ConfigMap and mounting it in your container as a file or directory. You can then access the configuration data stored in the ConfigMap using standard file I/O operations inside your container. This approach is useful when you have a larger amount of configuration data that you need to pass to your application, or when you want to keep the configuration data separate from your application code.
Step-1 Create a file and write your code into it:

Step-2 Now add this file to Configmap:

Step-3 You can Verify this with the following command:

kubectl get configmap

Step-4 Create a configuration file and map this as a volume:

Step-5 Apply this and verify this file in node:

You can see my_config file is present inside /tmp/config path in the node
2.ConfigMap - Environment Variables:
This approach involves creating environment variables from the key-value pairs in a ConfigMap and passing them to your container at runtime. You can then access the configuration data stored in the ConfigMap as environment variables inside your container. This approach is useful when you have a smaller amount of configuration data that you need to pass to your application, or when you want to easily override the configuration data using Kubernetes deployment settings.
Step-1 Create a config file and declare it as Environment variable.

Step-2 Apply this and verify this in Node:
Node-- #docker exec -it <container-id> /bin/bash
# ENV

When a ConfigMap is set as an environment variable, the contents of the ConfigMap are converted to environment variables with the keys and values from the ConfigMap. In this case, you won't be able to see the file itself because it has been converted to environment variables. You can only see the contents of the file by printing the value of the environment variable.
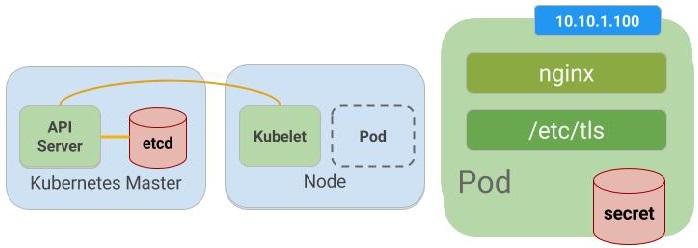
Secret:
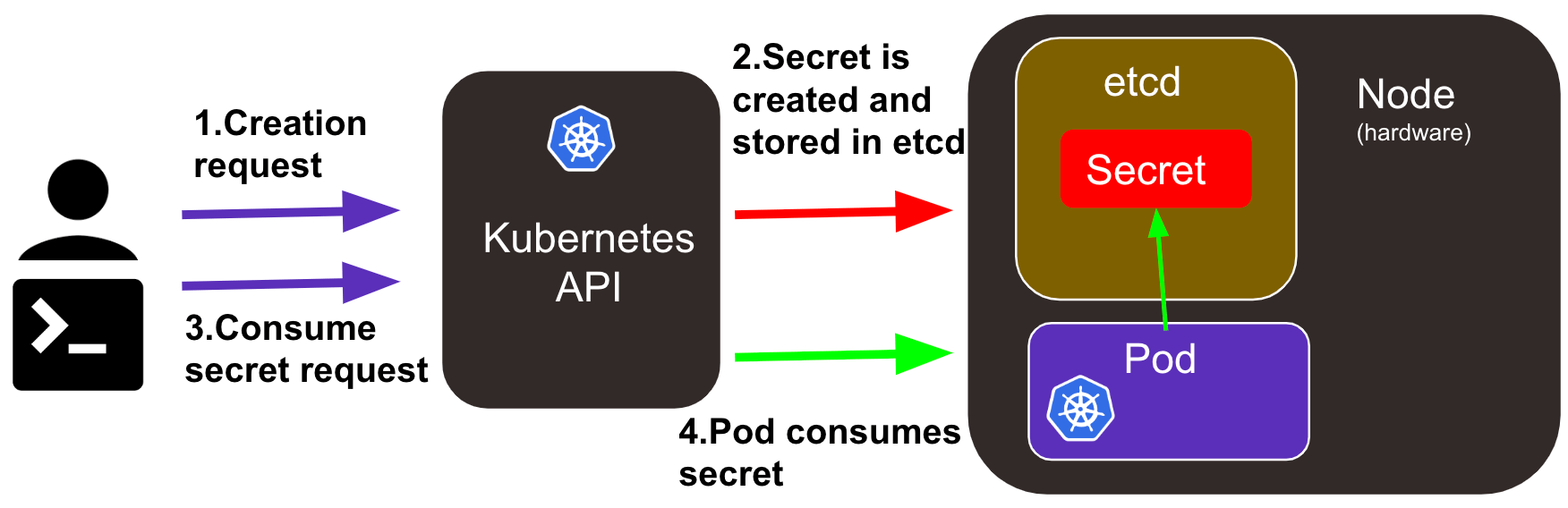
In Kubernetes, a secret is an object that allows you to store and manage sensitive information such as passwords, API keys, and other credentials. Secrets are encrypted and stored in etcd, the distributed key-value store used by Kubernetes.
Secrets can be used to pass sensitive information to pods in a secure way. They are mounted as volumes in a pod, and the information is made available to the application running inside the pod as files or environment variables. Secrets can also be used to authenticate and authorize access to Kubernetes resources, such as API servers, etcd, and other services.
1.Secrets-creating from literal values:
In Kubernetes, a Secret is an object used to store sensitive information such as passwords, tokens, and keys. Secrets are used to keep sensitive information secure by keeping it out of a pod's configuration file or environment variables. Instead, the sensitive information is stored in a Secret object, which can then be mounted as a file or exposed as environment variables in a pod.
Step-1 Create some file and add it to the secret:

Now add it :
kubectl create secret generic mysecret --from-file=<file1> --from-file=<file2>

Step-2 Create a deployment file and add the environment of secret:

Step-3 Apply it and verify it in node:


On Master Node it is showing that there are two files but they are opaque you can't see the content of it
Now check it on Node, you can access the content.

2.Secrets- from encoded data
Step-1 choose a password and convert it to base64 as shown in below example:
$ echo -n 'Abhijeet Born to Fly' | base64

Step-2 Now create a yml file and define it :


Check it using:
kubectl describe secrets

You will see a password in 20 bytes:
Step-3 Now change the deployment file to include this secret as an Environment variable:


Apply this and run:

Step-4 Switch to Node and check it:

+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++

